Software solution
AURUM
Corporate risk and compliance management
Target groups
- Companies
- Cities
- Auditors
- Risk managers
How can the IT security risk be reduced cost-effectively?
The intensive use of networked and complex IT systems has led to risks for companies, which can have serious legal and financial consequences. The efficient management of IT risks has become a mandatory requirement for the reliable operation of a company. Established procedures, based on standards, standards and experts, can in principle support companies in the management of IT risks. The manual review of risks and especially their numerous dependencies (for example with checklists) is, however, very time-consuming and error-prone. In addition, such a review is a snapshot that can be outdated hours later. Compliance with legal frameworks (eg GDPR) must be done automatically by modern compliance management systems.
Decision makers are often overwhelmed with the high number of possible countermeasures and not sure whether their IT security investment pays off or the solution found is suitable for the company. AURUM helps companies identify the best IT security concepts by looking at IT risk and compliance issues in an integrated way. It takes into account the costs and benefits of IT security measures as well as compliance with legal requirements and industry standards. The intuitive user interface and the innovative data and knowledge networking minimize the necessary interaction between user and system. The system is highly customizable and can be used by large enterprises and SMEs alike.
SOFTWARE
LOOK INSIDE
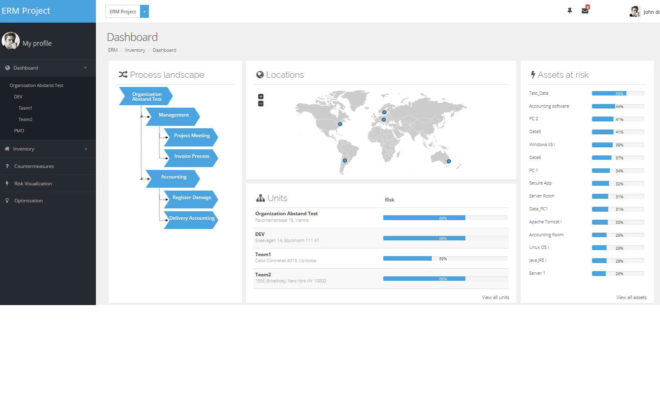
Intuitive dashboard with customizable widgets
The AURUM Dashboard summarizes the latest information for a quick overview. The dashboard consists of widgets that can be individually combined and rearranged using drag & drop. It provides an overview of the current company portfolio and the risk values determined. AURUM supports the administration of any number of sites. Access to the sites can be easily done via a zoomable map. This is created dynamically based on the addresses or GPS coordinates.
LOOK INSIDE
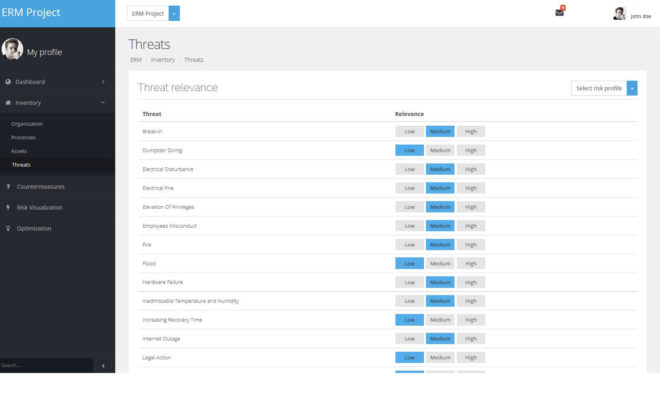
Consideration of dependencies and compatibility
A threat requires an existing and unprotected vulnerability to cause damage to a resource. A human threat can be realized either intentionally or unintentionally. Although existing standards and best practices often provide exemplary threat lists, there is occasional uncertainty about the precise threat characteristics of the Risk Manager. Which threats endanger my critical resources? What threats are multipliers by triggering other threats? What vulnerabilities are necessary for a particular threat to cause harm? AURUM allows the user to calculate probabilities for all selected threats regarding their enterprise-specific implementation based on the threat environment and the countermeasures already implemented. Prefabricated profiles allow a quick start.
LOOK INSIDE
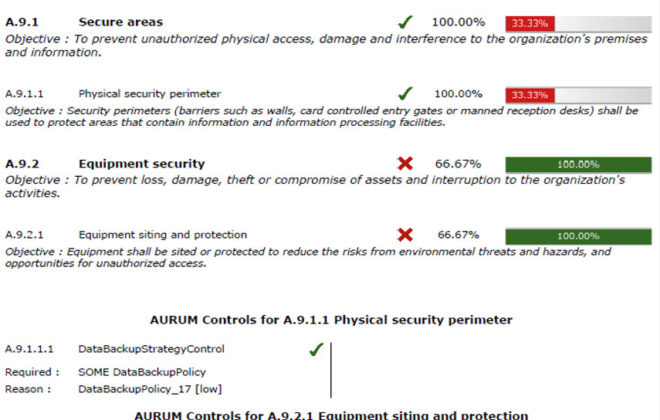
Central knowledge base
AURUM is based on a semantic knowledge base, which links all relevant information about possible IT security concepts, the company and its structure, processes and infrastructure. Inventory for business processes allows the administration and visualization of BPMN processes. Currently, AURUM includes over 500 information security concepts (threats, vulnerabilities, countermeasures) and automatically links them to the modeled enterprise data through semantic structures. This enables automated statements about the current level of risk and concrete suggestions for improvement.
LOOK INSIDE
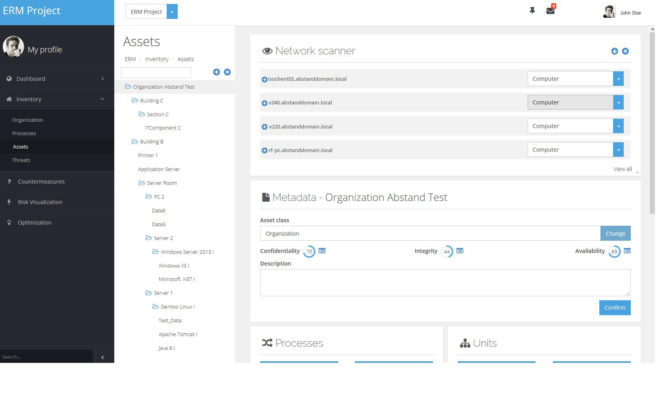
Inventory
The AURUM network scanner enables the automatic identification of relevant IT systems in the corporate network. Similarly, the policy scanner allows identification of existing security policies. The scans help the user with the initial and ongoing inventory of company resources. The automated approach, unlike the manual approach, prevents individual resources from being overlooked.
LOOK INSIDE
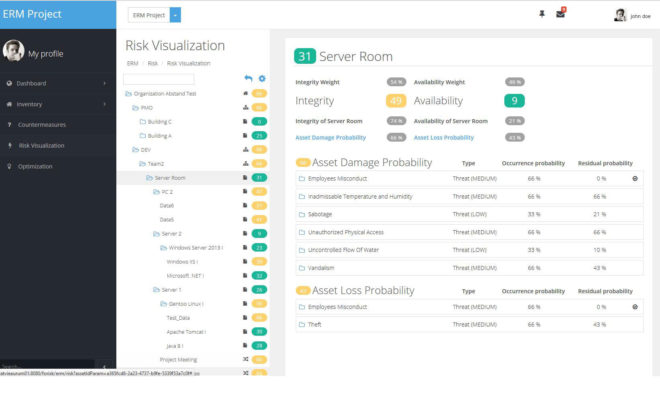
Visualization of the risk in real time
The risk visualization provides a quick and easy overview of the calculated risk level of organizational units, business processes and resources. In addition, it provides an aggregation of the risk level for individual organizational units and processes. In addition, AURUM calculates the company's risk level in real time. The resources, the probability of occurrence of certain threats, the currently implemented countermeasures, current events, etc. are taken into account. The visualization breaks down the impact of the threats into three categories: confidentiality, integrity, and availability.
LOOK INSIDE
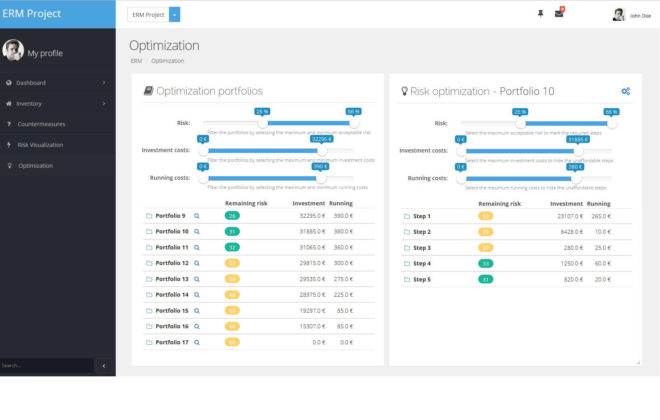
Interactive scenario analysis
AURUM provides a central knowledge base for the company. On the basis of this data, the calculation of proposals for the optimal allocation of (IT) resources takes place. For example, it optimizes the investment costs and the running costs required to achieve the desired level of protection. However, AURUM does not confront decision makers with a single solution. Rather, it offers the opportunity to explore different scenarios in a playful way and to become familiar with the consequences of this decision. The interactive user interface allows decision makers to analyze the problem. At the same time, AURUM ensures that decision makers are faced with efficient solutions. The result is a representation of the measures required to close the gap between the current situation and the desired level of risk (gap analysis).
LOOK INSIDE
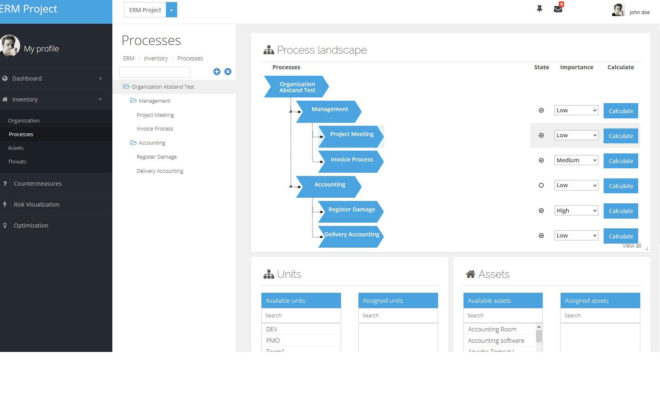
Business process-based risk management
AURUM allows the use of business processes as the basis for risk management. The processes can be imported from popular tools like Aris and Adonis. Alternatively, AURUM offers the possibility to define the processes as BPMN models. As usual from familiar business process management tools, AURUM visualizes the processes on the screen. Users can integrate the processes into the corporate structure and assign properties. Likewise, resources that have already been deposited, such as IT systems or important data, can be automatically identified via the processes. Thereafter, the business processes serve as the basis for the calculation of the risk level as well as the potential countermeasures.